
End-to-end Encryption is a popular term used by many big tech companies these days. We have seen big tech companies like Apple, Google, Meta, and Microsoft use this “End-to-end Encryption” in their apps or services or during a keynote of a major event. End-to-End Encryption is also sometimes referred to as E2EE.
It is a system of communication where only the sender and the receiver will be able to read the message and not any other third parties. Many popular apps and services use E2EE for communication over messages as well as calls. In this article, we will learn more about End-to-end Encryption starting from its definition and then we will take a look at how End-to-end Encryption works. Lastly, we will also take a look at how it protects and the advantages and disadvantages of this service. Let’s get started.
What is End-to-end Encryption?
Before we jump into the meaning of End-to-end Encryption, let us take a look at what data encryption means. Data encryption is the process of using an algorithm to transfer regular text characters into an unreadable format. This process uses encryption keys to scramble data so that only authorized users can read it.

End-to-end encryption uses this same process too, but it takes a step further by securing communications/messages from one endpoint to another. End-to-end encryption prevents any third parties from accessing data while it’s transferred from one user device or another device. End-to-end Encryption is also popularly known as E2EE.
Also Read: [Explained] What is Card Tokenization? How it Works, Benefits, Risks, and More
How Does End-to-end Encryption Work?
The End-to-end Encryption process starts with cryptography, which is a method for protecting information by transforming it into an unreadable format called ciphertext. Only users who possess a secret key can decrypt the message into plaintext. With E2EE, the sender or creator encrypts the data, and only the intended receiver or reader can decrypt it. Not even hackers or other third parties can access the encrypted data on the server, which makes the data extremely safe. E2EE provides the gold standard for protecting communication.
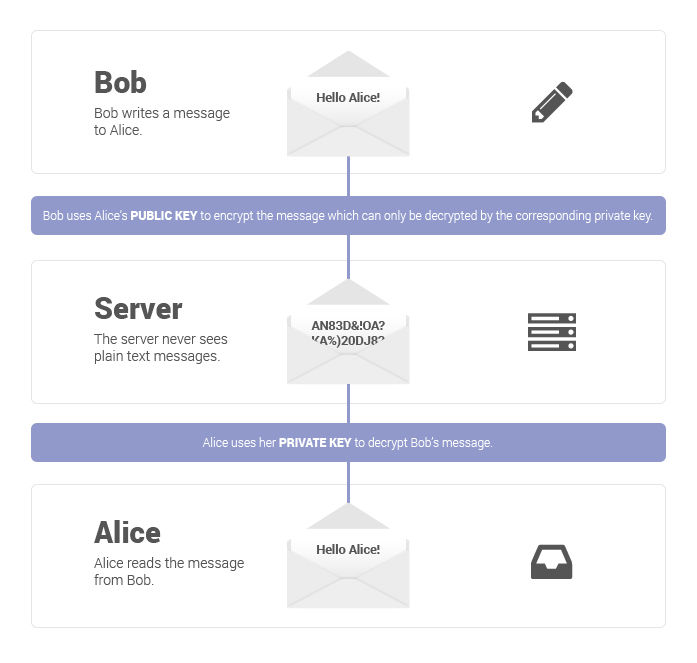
In End-to-end encryption, the encryption happens at the device level. Meaning, that the messages and files are encrypted before they leave the phone/computer and aren’t decrypted until it reaches their destination, which can be another phone/computer. This is one of the main reasons that hackers cannot access data on the server because they do not have the private keys to decrypt the data. The secret keys are stored with the individual user on their device which makes it much harder to access an individual’s data as well.
The security behind end-to-end encryption is enabled by the creation of a public-private key pair. This process is known as asymmetric cryptography. Asymmetric or public-key cryptography encrypts and decrypts the data using two separate cryptographic keys. The public key is used to encrypt a message and send it to the public key’s owner. Thereafter, the message can only be decrypted using a corresponding private key, also known as a decryption key.
In end-to-end encryption, the system creates public and private cryptographic keys for each person who joins.
How Does End-to-End Encryption Different From Other Types of Encryption?
Compared to other systems, End-to-end Encryption offers encrypting and decrypting of messages at endpoints only, which is on the sender’s and receiver’s devices. The usage of single-key/secret key encryption provides an unbroken layer of encryption from sender to recipient, but it uses only one key to encrypt messages. E2EE also makes sure that the messages are secure and safe from hacks. Since the E2EE messages can’t be read on any servers, providers like Google, Apple, Microsoft, etc won’t be able to look into your data.
These aforementioned additions make End-to-end Encryption different from any other type of encryption.
What does E2EE Protect Against?
With E2EE, messages sent can only be read by the receiver who has the keys to decrypt the message. This means no one can read the messages even on the server because they do not have the private keys to decrypt the data. Only the recipient can read the message. Next, End-to-end encryption also protects against tampering with encrypted messages.
What Doesn’t E2EE Protect Against?
While the key exchange is considered unbreakable using known algorithms, there are certain things that E2EE doesn’t protect from. The following can be considered as some of the weaknesses of E2EE.
Also Read: Telegram Channels: How to Find and Join Telegram Channels on Android, iOS Mobiles and PC
Metadata
While E2EE protects the actual message, the metadata such as date, time, and participants in the exchange are not encrypted.
Endpoint Security
As said multiple times, E2EE only protects data between the endpoints, This means the endpoints themselves are vulnerable to attack. This is also one of the prime reasons for enterprises to implement endpoint security to prevent data misuse and protect data beyond in-transit.
Man in the Middle Attacks (MITM)
Although a hacker can’t read any message in transit, he/she can impersonate the intended recipient, swap the decryption key and forward the message to the actual recipient without being detected.
Also Read: SBI KYC Update Online: How to Submit State Bank of India KYC Documents Online to Update Your Account
Advantages of End-to-end Encryption
- High level of privacy for all data
- Tamper-proof
- Ensures your data is secure from hacks
- Protects admins during any attack
- No unauthorized third party will have access to the information
Advantages of End-to-end Encryption
- Complexity in defining the endpoints
- Visible metadata
- Endpoint security
- Difficult backup scenarios
Popular Apps and Services with E2EE
Now that you are aware of what E2EE is and how it works, here are some of the popular apps and services that use E2EE.
- Zoom
- Signal
- iMessage
- Telegram (optional feature)
- Viber
- Microsoft Teams
- Microsoft Outlook
- Mega
- Google Messages (one-to-one communication)
- Facebook Messenger’s Secret chat
- ProtonMail
Also Read: Masked Aadhaar Card: How to Create Masked Aadhaar Card Using Different Methods













